$300 Million stolen – This staggering figure is the result of one of the largest social engineering attacks to date targeting a Trezor wallet user. In a recent collaborative investigation, BitcoinVN and its partners at leading Web3 Security & Crisis Response firm zeroShadow uncovered this massive cryptocurrency heist, which included $100M in BTC and $200M in LTC.
More than just a costly cautionary tale for the community, this case serves as a vivid demonstration that in the Web3 era, real-time intelligence sharing is the most effective defense for combating financial crime.
How the “Value Wallet” support scam works
This attack was not a hack; it did not exploit a bug or technical weakness. Instead, it took advantage of people’s trust in corporate branding and inability to discern authentic support staff.
The scam followed a common but very effective process:
Fake support messages
Scammers pretended to be Trezor support staff for a fabricated “Value Wallet” program. They contacted victims through social media, chat apps, or fake websites that looked official.
Creating fear and urgency
Victims were told there was a problem with their wallet, such as:
- suspicious activity
- a required firmware update
- an urgent security issue
They implied urgency, pressuring victims to act fast without double-checking.
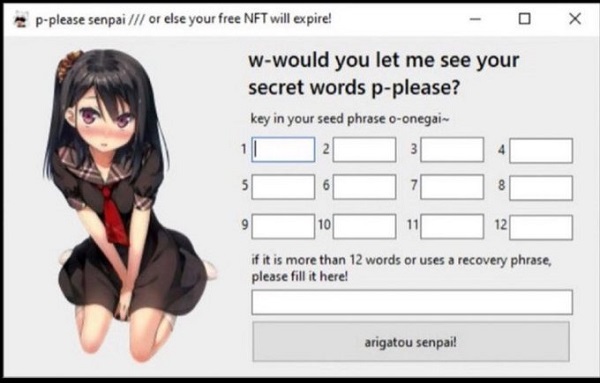
Stealing the seed phrase
The scammer asked for the seed phrase, saying it was needed to verify or recover the wallet. Once the seed phrase was shared, the attacker had full access to the wallet.
Swiftly moving funds to hide tracks
After taking control, the attacker quickly moved the funds through various instant swap services, to obscure their origin. The final step was an attempt to swap the assets into Monero (XMR) to make them untraceable.
Key security lesson: Your seed phrase is your wallet. No real support team will ever ask for it – ever.
How to protect yourself?
To protect your assets, always adhere to the following principles:
- NEVER share your seed phrase with anyone, under any circumstances.
- Assume all unsolicited “support” messages are scams.
- Verify information only from the official sources of your wallet provider.
- Use hardware wallets properly: store them offline, do not take screenshots, and avoid cloud backups (such as Google Drive or iCloud).
- Slow down: sense of urgency is a classic weapon used by scammers.
BitcoinVN’s role in responding to the attack
As soon as unusual activity was detected, BitcoinVN reported it to Web3 Cybersecurity Services firm zeroShadow, and worked with ecosystem partners to immediately track the money on the relevant blockchains.
Thanks to this fast action, the zeroShadow team was able to quickly trace the flow of funds in real time. Within just 20 minutes, they successfully froze over $700,000 USD before the assets could be swapped into Monero (XMR) – a privacy-focused coin that is very hard to track.
So far, approximately $2 million USD has been traced and attributed.
Remarkably, this process happened without needing court orders or months of paperwork.
Instead, it relied on Web3 companies sharing information instantly to catch the thieves before they could hide their tracks.
As CyberSecurity expert ZachXBT has said:
The zeroShadow team also confirmed that this is how Suspicious Transaction Reports (STR) work in the crypto era: identify, share, and act before the assets disappear.
BitcoinVN Consulting: Protecting your assets
The $300 million attack highlights a structural issue in today’s Web3 security landscape:
Many existing KYC/AML frameworks were designed for a different era and introduce risks of their own. Large-scale collection and long-term storage of sensitive personal data creates centralized honeypots that are increasingly targeted by sophisticated threat actors.
At BitcoinVN Consulting, we see this case as real-world proof of two things:
- Social engineering (the exploitation of trust) remains the dominant attack vector in crypto.
- Modern, network-level response systems can detect, flag, and contain illicit activity faster than legacy, document-heavy compliance processes – without increasing users’ personal data exposure.
At BitcoinVN Consulting, our role goes beyond advisory work. We operate as a frontline security partner for individuals and organizations navigating digital-asset risk.
By monitoring transaction flows and working closely with specialized blockchain intelligence and incident-response partners such as zeroShadow, we are committed to protecting the community from sophisticated financial attacks.
Don’t wait until your assets are lost to find a solution. Contact us for advice on safe storage and professional CyberSecurity and Operational risk management.
Conclusion
The “Value Wallet” scam caused significant losses. More importantly, it exposed a hard reality: financial crime is not stopped by paperwork or slow, standardized procedures. It is stopped when information moves fast and experienced actors coordinate in real time across the ecosystem.
Outdated, one-size-fits-all approaches to combating financial crime are easily exploited by sophisticated, well-funded threat actors. What actually works is speed, precision, and collaboration between competent teams who understand both the technology and the threat landscape.
For end users, however, the advice remains unchanged and cannot be repeated often enough: stay paranoid. Build a secure setup before you need it. Once funds are lost, options narrow quickly – and no response system can undo all damage after the fact. Prevention remains vastly more effective than any cure.



