A new security vulnerability called EvilLoader was discovered on Telegram, allowing hackers to spread malware and steal user data. With a library of malware at its disposal, EvilLoader poses a serious threat to unsuspecting Telegram users.
Telegram acted fast, and the exploit was patched within 48 hours. But when it only takes a minute to lose everything, it’s important to be vigilant against such threats.
In this article, we will take a closer look at how EvilLoader works, its impact, and the essential measures to protect against similar attacks.
What is EvilLoader?
EvilLoader is a type of malware specifically designed to hide on the victim’s computer. It silently downloads and installs other malicious software from the internet under the hacker’s command. While EvilLoader does not cause immediate harm, it acts as a “gateway” for more dangerous malware, allowing hackers to control or steal data from the infected device.
The types of malware that EvilLoader can download include viruses that steal banking information or crypto, spyware that records keystrokes (keyloggers), or ransomware, which encrypts data and demands a ransom. In short, EvilLoader is a dangerous tool that silently paves the way for cyberattacks, potentially causing significant financial and data security damage.
How does EvilLoader work?
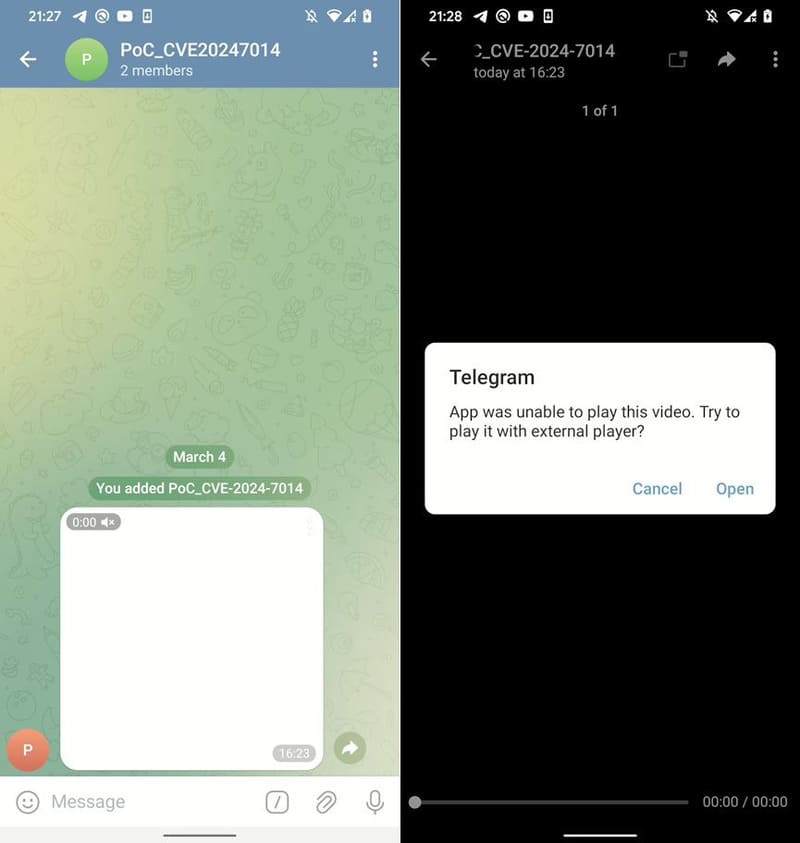
EvilLoader infiltrates the victim’s device through a malicious attachment sent in Telegram. The file, an html file disguised as mp4 video, uses an exploit to execute javascript to install itself on the victim’s device. Once installed, it hides within the system to avoid detection by antivirus software.
It then connects to the hacker’s server, waiting for instructions to download additional types of malware, such as trojans that steal login credentials, ransomware that encrypts files and demands ransom, or spyware that monitors user activity.
The malware carries out its tasks depending on the type of malicious software it downloads. This can include stealing passwords, tracking user activities, or encrypting files to demand ransom.

Note: Simply opening the file, without the need for further prompt, is enough to infect your phone.
Why is EvilLoader dangerous?
- Hard to detect: It operates stealthily, avoiding detection by antivirus programs.
- Downloads various types of malware: Not just one, but several types of malware, depending on the hacker’s goals.
- Easily spreads: It sends itself out to the contacts of infected victims in order to spread further.
- Steals important data: This includes banking information, email, passwords, and even sensitive documents.
How does EvilLoader affect cryptocurrency users?
- Stealing crypto: EvilLoader can deliver malware that tracks what you type, like your passwords and private keys for crypto wallets and exchanges. This allows hackers to steal your crypto.
- Taking over crypto accounts: Once installed, EvilLoader can give hackers control of your device, letting them take over your cryptocurrency accounts, make transactions, or change security settings.
- Ransomware risk: Some versions of EvilLoader may install ransomware that locks your files, including important crypto info. Hackers then demand payment in cryptocurrency to unlock them.
- Spreading in crypto communities: If someone in a crypto group (like on Telegram or Reddit) gets infected, EvilLoader can spread to others, risking many wallets and funds.

How to prevent EvilLoader?
- Be cautious with attachments: Avoid opening files from unknown senders, especially attachments sent through platforms like Telegram or email. Malicious files can contain malware like EvilLoader, so be careful with what you download.
- Keep software updated: Always update your operating system, apps, and antivirus software. Updates often fix security vulnerabilities, reducing the risk of malware like EvilLoader taking advantage of flaws.
- Use strong antivirus and anti-malware software: Install reliable antivirus software and keep it updated. Regular scans help detect and remove malware like EvilLoader before it causes damage.
- Enable Multi-Factor Authentication (MFA): Enable MFA for important accounts, such as crypto wallets and online banking. Even if your password is compromised, MFA adds an extra layer of protection.
- Use a dedicated hardware wallet to keep your private keys isolated from everyday internet-connected devices.For trusted options, BitcoinVN Shop is the official authorized reseller in Vietnam for industry-leading brands such as Ledger, Trezor, Blockstream, and Coinkite.
- Avoid suspicious websites: Stay away from untrusted websites that may contain malware. Look for secure connections (https://) and avoid clicking on suspicious ads or links.
- Educate yourself and others: Stay informed about common scams and malware. Educating yourself and those around you helps reduce the risk of falling for phishing or other attacks.
- Back up your data: Regularly back up important files to a secure location. This helps protect your data in case of a ransomware attack or system infection.
- Use a Virtual Private Network (VPN): Use a VPN to encrypt your internet connection and protect your privacy, especially on public Wi-Fi. A VPN helps secure your device from malware attacks like EvilLoader.
Conclusion
In conclusion, the EvilLoader vulnerability discovered on Telegram is a serious threat that can steal sensitive information. By staying cautious, keeping software updated, and using strong security measures, you can protect yourself from this malware.
Need further guidance?
Our in-house Cybersecurity team at BitcoinVN offers 1:1 consulting sessions designed to help you take full control of your digital assets – securely and confidently.
Whether you’re just getting started with self-custody, exploring advanced setups like MuSig, or want to harden your operational security, our experts will guide you step-by-step toward true self-sovereignty. No fluff, no shortcuts – just practical, Bitcoin-native security tailored to your needs.
🔐 Book your private session today at bitcoinvn.io/consulting